C#
Archived Posts from this Category
Archived Posts from this Category
Posted by Chris Alcock on 30 Oct 2007 | Tagged as: .NET, C#, Design, Development, Software, SysAdmin
One of my longest standing pet hates with desktop software developed in .NET relates to the almost inevitable security exception that will occur if you attempt to run it from a network share. Its always one of the first things I notice about software, as I often download and unzip software onto my desktop (which on my work machine is located on a network share) and then attempt to run it in place. Many large and quite impressive pieces of software that get distributed as .ZIP files rather than installers suffer this plight, and a lot of them don’t handle the exception well (One that springs to mind was the much heralded release of NDepend 2.0).
The good news is that this anguish may well be about to come to an end, as Brad Abrams requests feedback about the .NET teams possible plan to make network shares trusted. As he mentions, there really is no good reason not to trust a network share for running managed .NET code – there is no such protection for unmanaged code, and there is little or no way a normal user would be aware of which is .a NET EXE and which is unmanaged EXE.
To answer Brad’s Questions:
A) Have you ever run into this limitation (a security exception when running a .NET application from a network file share)?
I frequently experience these issues – I tend to use this problem (and if its been worked round in the application) as a yard stick as to how well written the application is.
B) How often do you use network file shares for deploying applications (managed or otherwise)?
Most of my development is web based, however for utilities written for in house use we tend to distribute them on a network share – being able to run these in place would be a great help, as updating them would be easier.
C) If you think we should make this change, when would be a good time? Is it something we should do sooner in a service pack of the .NET Framework or later in a full release of the framework. Note, we are DONE with .NET Framework 3.5, so there is zero chance it is getting in that release.
From my point of view a patch as soon as possible, and have it included in the next release of the framework – Since this is a relaxation of the current restriction, I can’t see that it would cause any more problems in terms of support of existing application, as a reduction of the support incidents caused by this issue would reduce.
D) Can you ask your local network admin what they think of this issue? Would they be in favor of this sort of change? If so, when?
This change should simplify deployment – allowing Managed EXE to run from shares should mean that local disks can be more locked down as there would be no need to copy programs locally to run them.
All in all, I’m very much in favour of this change – It will level the playing field, give a more consistent user experience, and reduce the problems people have with winforms applications.
Comments Off on Untrusted Network shares
Posted by Chris Alcock on 01 Oct 2007 | Tagged as: .NET, ASP.NET, C#, Development, Web Services, XML
One of my basic assumptions about the .NET framework was proved incorrect last week. Up until then, I had believed that when you are using the built in framework classes for exposing web services you were always safe when it came to the output being valid XML. Sadly that turns out to be untrue, and to make matters worse, .NET will happily output XML over a web service even its own .NET web service clients can’t read.
There are certain characters that are forbidden from being in XML as per the official specification. These characters are the low ascii characters such as NULL, EOF etc. Its important to note that this is not a case of unescaped/unencoded versions of this character being disallowed, the encoded characters are also disallowed.
The problem with this isn’t that the .NET framework doesn’t understand these rules – it manages just fine when it comes to acting as a client to a web service serving these characters in content, throwing nice exceptions explaining that these characters are invalid. Additionally, the XML Text Reader has a property ‘Normalization’ which causes the XML reader to be more liberal and ignore invalid characters – but this option is not used within the automatically generated Web Service Client.
This problem isn’t limited to just the web services, standard XML serialisation also experiences the same problems. Here are bits of code that illustrate the problem:
[WebMethod()]
public string InvalidCharacter()
{
return "" + (char)4;
}
public class MyClass
{
public string Test = "" + (char)0;
public static void Main()
{
MyClass c = new MyClass();
System.Xml.Serialization.XmlSerializer xs = new System.Xml.Serialization.XmlSerializer(typeof(MyClass));
System.Text.StringBuilder sb = new System.Text.StringBuilder();
System.IO.StringWriter sw = new System.IO.StringWriter(sb);
xs.Serialize(sw, c);
Console.WriteLine(sb.ToString());
System.IO.StringReader sr = new System.IO.StringReader(sb.ToString());
try
{
c = (MyClass)xs.Deserialize(sr);
}
catch (System.Exception ex)
{
Console.WriteLine(ex.ToString());
}
}
}
The little console application gives output like this:
System.InvalidOperationException: There is an error in XML document (3, 12).
System.Xml.XmlException: '.', hexadecimal value 0x00, is an invalid character.
Line 3, position 12.
Unfortunately I haven’t yet found a fix for this – my only solution is to work around the problem by ensuring that these invalid characters can’t get into the system in the first place or clean the text on the get of each property of the serialized objects.
Things like this really worry me – our frameworks shouldn’t be outputting things that they can’t read – let alone outputting things that completely contravene the specifications. As always, any suggestions on an alternative solution to this problem are welcome.
Posted by Chris Alcock on 17 Jun 2007 | Tagged as: .NET, C#, Community, Photography, Software
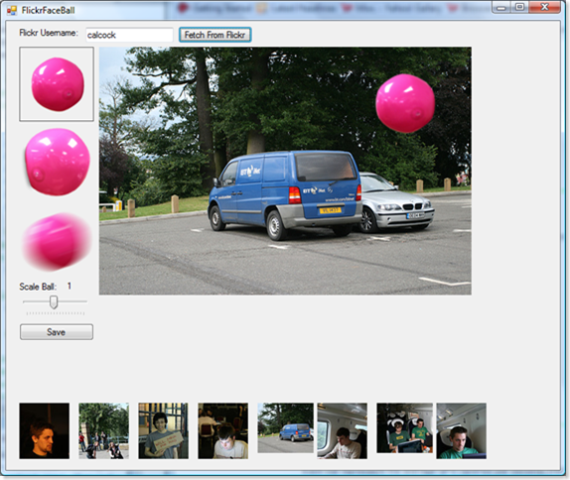
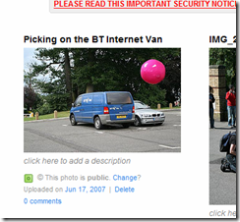
OK, the time has come to unveil my Hack for Yahoo Hack Day. Face Ball is the ‘Crazy new game at Flickr HQ‘, and images have been popping up all over flickr as other join in. Well now, you too can join in the fun, and just like Thom Shannon, make your own Face Ball images without risk of injury or special equipment.
Flickr Face Ball is a .NET 2 Windows Forms application that allows you to select images from you Flickr photo stream by tagging them as ‘ToFaceBall’, and add one of three different face ball images to the original photo, uploading the results to your Flickr account.
So, how do you get involved in this craze:
Credits:
FlickrFaceBall uses the Flickr.NET API Implementation – I have only good things to say about this library – it just works 😉
Thom Shannon for providing the inspiration for the Hack, and also providing the PSD of face ball images.
Finally, to the original source of the Face Ball images – photo1 and photo2
Please Note: This program is hack quality code – It’s not been tested much, and if it breaks your computer, flickr account, or anything else, its your own responsibility.